A large number of businesses and organisations have workloads on-premises and in the cloud. In this Hybrid approach there are times that users in your corporate office need to be able to access services hosted on AWS and many more use cases (like extending Active Directory to AWS).
By default, instances that you launch into an Amazon VPC can’t communicate with your On-premises network. You can enable access to your remote network (and the opposite) from your VPC by creating an AWS Site-to-Site VPN connection. That way you can securely access your on-premises environment from AWS environment and vice versa.
Although there are more ways to achieve that, the Site-to-Site VPN connection is the much and faster to implement, plus is the most cost effective way.
Below is a diagram of a AWS Site-to-Site VPN connection with an On-premises network
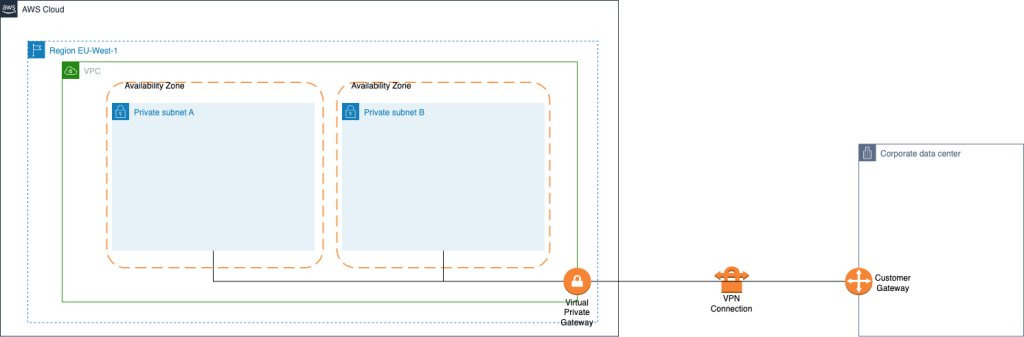
Let’s have a look in the components and the security used:
- Virtual Private Gateway (VGW): is a logical gateway object, which is a target of one or more Route Tables.
- Customer Gateway (CGW): is a logical configuration on AWS, which represents the configurations of the physical on-premises router where VPN is connected to
- VPN connection: A secure connection between your on-premises equipment and your VPCs.
- VPN tunnel: An encrypted link where data can pass from the customer network to or from AWS.
- IPsec: This type of VPN uses the Internet Protocol Security (IPsec) protocol to establish a secure connection between your on-premises network and your VPC. IPsec is a widely-used, industry-standard protocol that provides strong encryption and authentication.
You can use a PresharedKey or certificates, during the deployment, to authenticate your Site-to-Site VPN tunnel endpoints and the pre-shared key is the default authentication option.
One of the key steps in configuring Site-to-Site VPN is choosing the routing protocol to use. AWS supports two routing protocols: Border Gateway Protocol (BGP) and static routing.
BGP is a dynamic routing protocol that automatically updates routing information and adapts to changes in the network. It’s typically used in large, complex networks and is more suited to environments with a high degree of network churn. BGP also allows for automatic failover, which can be useful in case of link failure.
Static routing, on the other hand, uses manually-configured routes, rather than dynamically learned routes. It’s a simpler, more straightforward protocol that’s well-suited to small or stable networks. Static routing is easy to set up and manage
To configure Site-to-Site VPN with BGP, you will need to create a Virtual Private Gateway (VGW) and attach it to your VPC. Next, you will need to create a Customer Gateway (CGW) on your on-premises network and configure it with the appropriate settings. Then, you will need to create a VPN connection between the VGW and the CGW and configure BGP on both ends.
To configure Site-to-Site VPN with static routing, you will also need to create a Virtual Private Gateway (VGW) and attach it to your VPC. Next, you will need to create a Customer Gateway (CGW) on your on-premises network and configure it with the appropriate settings. Then, you will need to create a VPN connection between the VGW and the CGW, but this time you will configure static routes on both ends.
There is also the option the option of using a Transit Gateway (TGW) instead of a Virtual Private Gateway and we will discuss that option in another post.
Routing Propagation
In order to implement dynamic routing, you need to implement the Route Propagation at the VPC router level. In addition to that, it is required to have the BGP support in the networks (at the physical router level) in order to have the router propagation feature.
With BGP, configured on both the on-premise and the AWS sides using Autonomous System Number (ASN), Network routing information is exchanged to both sides.
The following Cloudformation template can be used to deploy a site-to-site VPN, with some configurable options (Like BGP or Static routing). This is for demonstration purposes, to quickly deploy a VPN and you can adapt it as per your requirements
AWSTemplateFormatVersion: '2010-09-09'
Description: >-
Cloudformation template to create a Site-to-Site VPN on AWS
Metadata:
AWS::CloudFormation::Interface:
ParameterGroups:
- Label:
default: CGW configuration
Parameters:
- BgpAsn
- CGWIPAddress
- Label:
default: VPG configuration
Parameters:
- PrivateRouteTable
- Label:
default: VPN configuration
Parameters:
- StaticRoutesOnly
- PreSharedKey
- Label:
default: Tags
Parameters:
- pTagName
ParameterLabels:
Type:
default: CGW Type
BgpAsn:
default: BGP ASN (Use Default value)
StaticRoutesOnly:
default: Use for Static Routing
PreSharedKey:
default: Type the PreSharedKey
Parameters:
BgpAsn:
Default: '65000'
Description: Enter the BGP ASN
Type: Number
MinValue: '1'
MaxValue: '65534'
StaticRoutesOnly:
AllowedValues:
- "true"
- "false"
Default: "false"
Description: Set to "true" for devices that don't support BGP
Type: String
CGWIPAddress:
Description: Enter the IP for CGW
Type: String
PreSharedKey:
Description: Enter the PreShared Key
Type: String
NoEcho: "true"
PrivateRouteTable:
Description: The Private Route Table id, in your VPC
Type: String
pTagProductName:
Type: String
Description: Enter the Product Name
Resources:
CustomerGateway:
Type: AWS::EC2::CustomerGateway
Properties:
Type: ipsec.1
BgpAsn: !Ref BgpAsn
IpAddress: ! Ref CGWIPAddress
Tags:
- Key: Name
Value: !Sub ${pTagName}-CGW
VPNGateway:
Type: AWS::EC2::VPNGateway
Properties:
Type: ipsec.1
Tags:
- Key: Name
Value: !Sub ${pTagName}-VPG
VPNGatewayRoutePropagate:
Type: AWS::EC2::VPNGatewayRoutePropagation
Properties:
RouteTableIds:
- !Ref PrivateRouteTable
VpnGatewayId: !Ref VPNGateway
VPNConnection:
Type: AWS::EC2::VPNConnection
Properties:
Type: ipsec.1
StaticRoutesOnly: !Ref StaticRoutesOnly
PreSharedKey: !Ref PreSharedKey
CustomerGatewayId:
!Ref CustomerGateway
VpnGatewayId:
!Ref VPNGateway
Tags:
- Key: Name
Value: !Sub ${pTagName}-VPN